In 2020 I had more time than usual to work on geocaching puzzles. I used the time to create a geocache based on spies that I had been mentally planning for a long time. This is a long post, and you will find the tech items at the end.
Picking the Theme
Working on spies and numbers stations can cover time from the mid 20th century to the present. Numbers stations are shortwave radio transmitters that send long lists of numbers, believed to be messages to government agents around the world. One station in particular, known as the Lincolnshire Poacher, used an especially catchy tune. To make it buildable and findable I did not want to use special shortwave radio signals. FM broadcast band transmitters are easy to use and receive.
The puzzle needed the excitement of tracking a real spy before the agent was able to carry out a damaging mission.
I needed to make it (mostly) historically accurate, allowing the cacher to play the U.S. government agent tasked with stopping the enemy spy. If I made it modern the spy vs. spy action would be too high tech to be simple fun for a geocacher.
Working within this list of rules, I determined the game would take place in the summer of 1945. This was the beginning of the cold war after Germany was defeated, but the U.S. was still fighting in the pacific and war production remained important. Finally, this was the time when the FM radio band in the U.S. changed. This little bit of trivia allowed me to use a common FM transmitter to create a spy station that would have been heard by almost no one in 1945.
Creating the Story
I spent some time researching historical spy action during the second world war and just afterward. I explored the OSS, FBI, and FCC and their duties. The OSS would have operated outside the U.S. with the FBI handling domestic duties. The FCC actively aided military and intelligence agencies with radio direction finding and seeking out rogue transmitters. That would make our cacher an FBI agent using info from the OSS and the FCC. Soviet spies were actually caught in Canada during the period, so I worked off that news story and created my piece of historical fiction following a soviet agent from occupied Germany, through Canada, and into the U.S.
The cache’s page starts by placing the geocacher into the summer of 1945:
It is August 1, 1945. You are an FBI agent working in York County, PA. With spirits still lifted by VE day the citizens of York are focusing their efforts toward VJ day. Relations between the Soviet Union and the other Allies continue to deteriorate but you have more immediate worries, having just received a new assignment from Washington D.C. concerning Soviet NKGB agent activity in the area. While foreign agent activity is alarming enough, this case looks like it could be far more dangerous. The safety of the entire area’s population and its vital manufacturing contributions to the war effort are all in your hands.
Making the Documents
I wanted a story that gradually unfolded as the geocacher worked through the case files and did some investigation. That required more room than a typical cache page on geocaching.com. I created a web site for the puzzle. It allows the cacher to work through a series of web pages reading the case file documents and tracking the spy from Germany to Canada, to New York, and then to the climax of the chase. I also found an online scan of a real FBI internal newsletter from 1945, which I edited to include puzzle hints for the geocacher. This OSS memo is the first document in the case file, explaining the start of the hunt for NKGB agent Viktor Mikhailovich. I used historically correct formats for the documents I created when possible.
Bringing the Chase to Life
I wanted the cacher to solve a real numbers station puzzle to find the cache. Numbers stations are assumed to use One Time Pad (OTP) encryption, which can not be solved without the matching key pad. This also means that the encoded message could be anything with the right key pad. I found a real recording and created the correct key to have the broadcast decode with my message. I also created two additional geocaches, Agent Lesson 1 and Agent Lesson 2, as instructions for solving this kind of encryption. Cachers could try it alone or go to school and know what to do.
The Thing That Explodes
All good spy stories have the race against certain destruction adding excitement, so I added that as the final cache container. The NKGB agent carries an unknown piece of unstable military hardware. Can the geocacher find and disarm the device in time?
Enough Story! Where Are the Gadgets?
I won’t go through the entire story here, but the puzzle flow requires multiple active steps by the cacher beyond the case files. Two of these are electronic gadgets.
The numbers station is a real FM transmitter that is only activated at particular times during the day. It turns off so there is no transmission, not even an empty carrier, at all other times. The cacher must determine when and where to receive the numbers station broadcast. The broadcast is stored in an MP3 file. I modified a UCTronics weather station kit to handle triggering the transmitter at the correct times. The kit, based on the ESP8266 module, was already programmed to be on a Wi-Fi network and keep its time synchronized with internet time servers for accuracy. I added some logic to detect the desired times each day and trigger an output to turn on the MP3 module and FM transmitter.
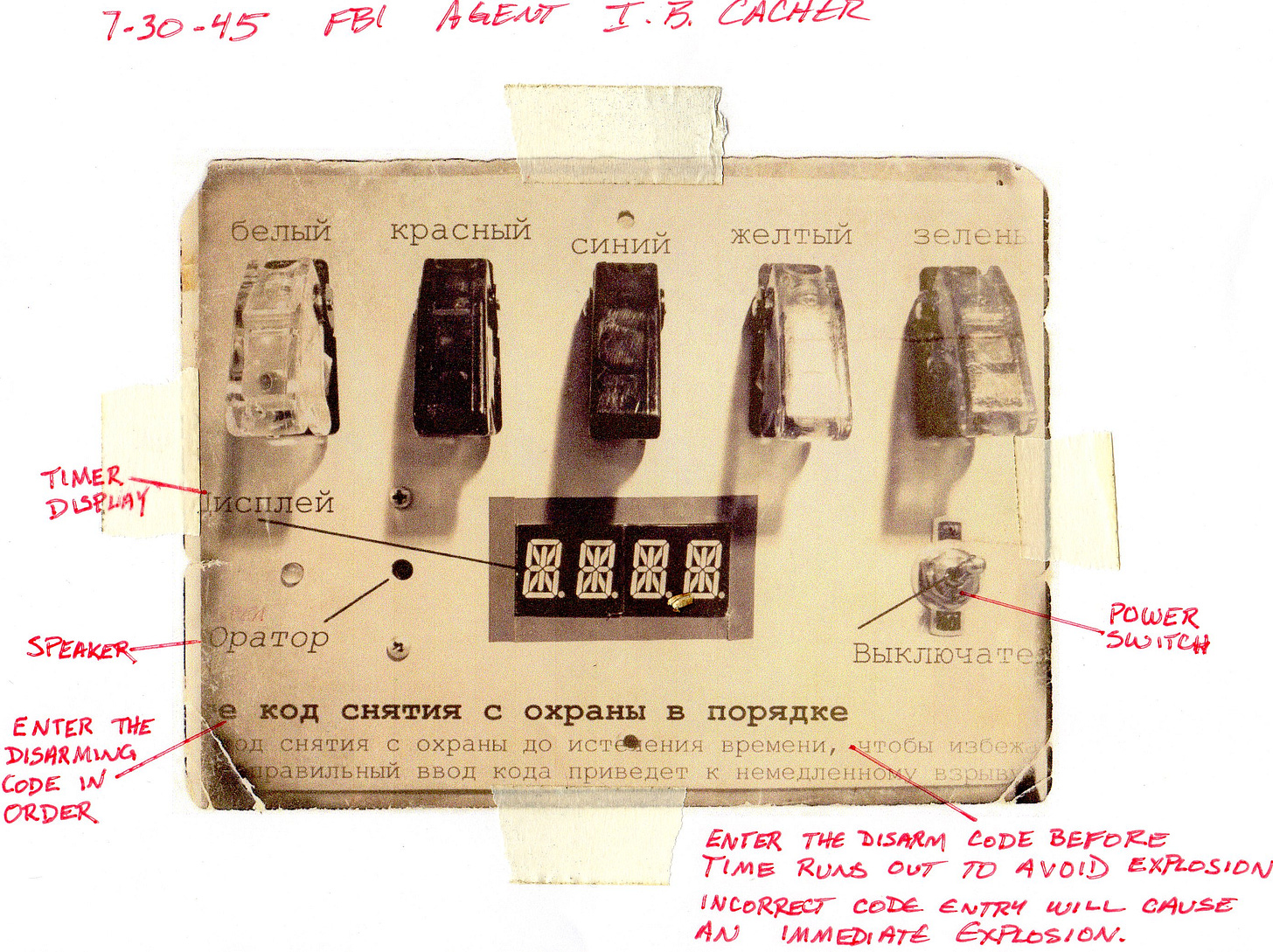
At the end of the chase is the main gadget puzzle. I repurposed a puzzle I created for a scout camp a few years ago. It is based on the Crypto Countdown project from Adafruit, but I converted it to use an Arduino and fit into an ammo can. This is the document recovered from the NKGB agent explaining the device with the FBI lab notes as found in the case file:
The puzzle is locked inside its travel case for safety. By the time a cacher knows the location of the final puzzle he or she will know how to open the case.
The gadget build is two ammo cans bolted together. A .50 cal can with the puzzle and a .30 cal can locked with the log and swag inside.
The finder must solve the puzzle and disarm the device before the time runs out in order to access the lock code for the log container.